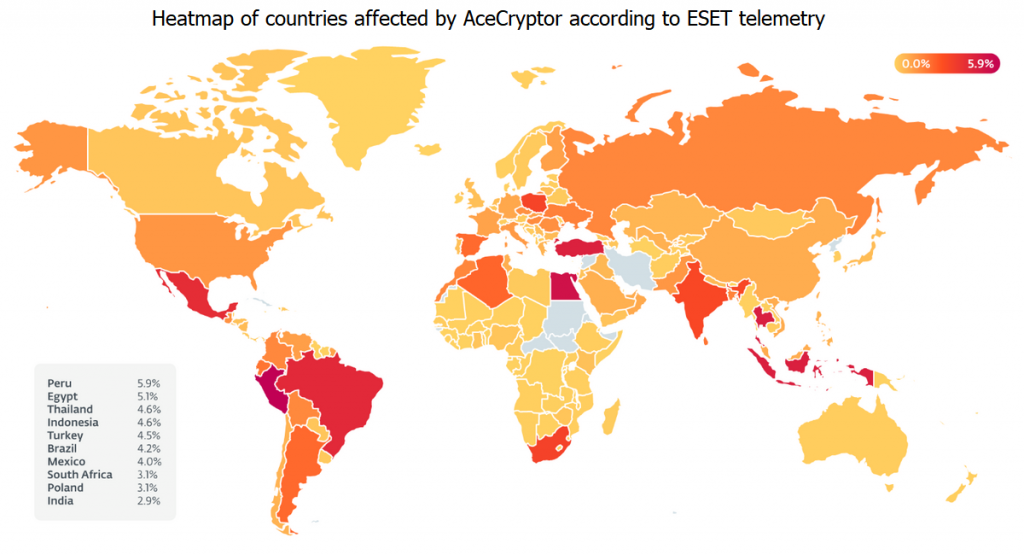
AceCryptor samples are very prevalent worldwide because multiple threat actors are actively using the.
ESET researchers revealed details about a prevalent cryptor malware, AceCryptor, which operates as a cryptor-as-a-service used by tens of malware families. This threat has been around since 2016, and has been distributed worldwide, with multiple threat actors actively using it to spread packed malware in their campaigns. During 2021 and 2022, ESET telemetry detected over 240,000 detection hits of this malware, which amounts to over 10,000 hits every month. It is likely sold on dark web or underground forums, and tens of different malware families have used the services of this malware. Many rely on this cryptor as their main protection against static detections.
“For malware authors, protecting their creations against detection is challenging. Cryptors are the first layer of defense for malware that gets distributed. Even though threat actors can create and maintain their own custom cryptors, for crimeware threat actors, it often may be time-consuming or technically difficult to maintain their cryptor in a fully undetectable state. Demand for such protection has created multiple cryptor-as-a-service options that pack malware,” says ESET researcher Jakub Kaloč, who analyzed AceCryptor.
Among the malware families found that used AceCryptor, one of the most prevalent was RedLine Stealer – malware available for purchase on underground forums and used to steal credit card credentials and other sensitive data, upload and download files, and even steal cryptocurrency. RedLine Stealer was first seen in Q1 2022; distributors have used AceCryptor since then, and continue to do so. “Thus, being able to reliably detect AceCryptor not only helps us with visibility into new emerging threats, but also with monitoring the activities of threat actors,” explains Kaloč.
During 2021 and 2022, ESET protected more than 80,000 customers affected by malware packed by AceCryptor. Altogether, there have been 240,000 detections, including the same sample detected at multiple computers, and one computer being protected multiple times by ESET software. AceCryptor is heavily obfuscated and has incorporated many techniques to avoid detection throughout the years.
“Even though we don’t know the exact pricing of this service, with this number of detections, we assume that the gains to the AceCryptor authors aren’t negligible,” theorizes Kaloč.
Because AceCryptor is used by multiple threat actors, malware packed by it is distributed in multiple ways. According to ESET telemetry, devices were exposed to AceCryptor-packed malware mainly via trojanized installers of pirated software, or spam emails containing malicious attachments. Another way someone may be exposed is via other malware that downloaded new malware protected by AceCryptor. An example is the Amadey botnet, which we have observed downloading an AceCryptor-packed RedLine Stealer.
Since many threat actors use the malware, anyone can be affected. Because of the diversity of packed malware, it is difficult to estimate how severe the consequences are for a compromised victim. AceCryptor may have been dropped by other malware, already running on a victim’s machine, or, if the victim got directly afflicted by, for example, opening a malicious email attachment, any malware inside might have downloaded additional malware; thus, many malware families may be present simultaneously.
AceCryptor has multiple variants and currently uses a multistage, three-layer architecture. Even though attribution of AceCryptor to a particular threat actor is not possible for now, ESET Research expects that AceCryptor will continue to be widely used. Closer monitoring will help prevent and discover new campaigns of malware families packed with this cryptor.