Between January 2023 and September 2024, Kaspersky Digital Footprint Intelligence experts identified 547 listings to buy and sell exploits targeting software vulnerabilities. These advertisements are posted on various dark web forums and shadow Telegram channels, with half involving zero-day and one-day vulnerabilities. However, it is difficult to confirm whether these exploits are functional, as the dark market is rife with scams. Additionally, Kaspersky found that, on average, the cost of exploits for remote code execution vulnerabilities amounted to $100,000.
Exploits are tools used by cybercriminals to take advantage of vulnerabilities in various software programs, like those from Microsoft, to commit illegal activities, such as gaining unauthorized access or stealing data. More than half of the dark web posts (51%) offered or sought to purchase exploits for zero-day or one-day vulnerabilities. Zero-day exploits target undiscovered vulnerabilities that software vendors have not identified and patched yet, while one-day exploits focus on systems that do not have the patch installed.
Anna Pavlovskaya, Senior Analyst at Kaspersky Digital Footprint Intelligence. “Overall, the exploit market remains stable; while activity fluctuates, the threat is always present. This highlights the need for cybersecurity hygiene practices, such as the regular patching and monitoring of digital assets on the dark web”.
“Exploits can target any program, but the most desirable and expensive ones often focus on enterprise-level software. These tools enable cybercriminals to carry out attacks, which equate to substantial gains for them, such as stealing corporate information or spying on an organization undetected. However, some exploit offers on the dark web may be fake or incomplete, meaning they don’t function as advertised. Additionally, a significant portion of transactions are likely to occur in private. These two factors complicate the assessment of the actual market volume for functional exploits,” explains Anna Pavlovskaya, Senior Analyst at Kaspersky Digital Footprint Intelligence.
The dark web market offers a wide array of different types of exploits. Two of the most widespread are those for RCE (Remote Code Execution) and LPE (Local Privilege Escalation) vulnerabilities. According to an analysis of over 20 listings, the average price for RCE exploits is around $100,000, while LPE exploits typically cost about $60,000. RCE vulnerabilities are considered more dangerous, as they allow attackers to take control of a system or its components, or confidential data.
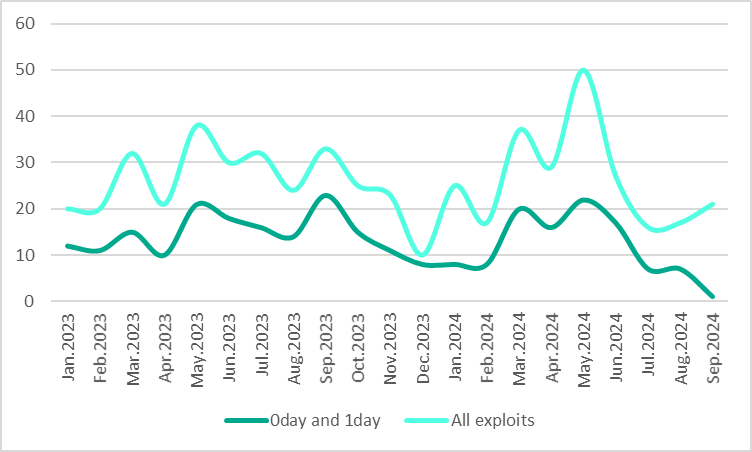
Dark web listings for buying and selling exploits, 2023-2024, where some offers can be repetitive. Source: Kaspersky Digital Footprint Intelligence
This year, the peak level in exploit sales and purchases occurred in May, with 50 relevant posts, compared to an average of about 26 per month in the period surrounding the surge. “Peaks in the exploit market’s activity are unpredictable and hard to link to specific events. Interestingly, in May, the dark web witnessed the sale of one of the most expensive exploits during the analyzed period – allegedly, for a Microsoft Outlook zero-day vulnerability priced at nearly two million US dollars,” – elaborates Anna Pavlovskaya. “Overall, the exploit market remains stable; while activity fluctuates, the threat is always present. This highlights the need for cybersecurity hygiene practices, such as the regular patching and monitoring of digital assets on the dark web”.
To counter threats related to vulnerabilities and exploits, the following measures are effective:
- Use services such as Kaspersky Digital Footprint Intelligence to monitor the dark web market for any relevant cyberthreats.
- Have strong endpoint protection that builds up your security with EDR and XDR from a trusted manufacturer whose products are verified by independent test labs, such as Kaspersky Next.
- Conduct regular security assessments to identify and patch vulnerabilities before they become an entry point for attackers.


