New malware variant combines Petya/NotPetya traits with advanced bootkit capabilities, raising red flags for future threats
ESET Research has revealed a new strain of ransomware called HybridPetya, capable of targeting modern UEFI-based systems and bypassing Secure Boot protections through a known vulnerability. While not yet active in the wild, the discovery underscores the growing sophistication of ransomware authors and their interest in exploiting firmware-level weaknesses.
The newly discovered samples were uploaded from Poland to VirusTotal in February 2025, appearing under filenames such as notpetyanew.exe. ESET researchers noted strong similarities to the infamous Petya/NotPetya malware that wreaked global havoc in 2017, causing an estimated $10 billion in damages. Unlike its predecessors, however, HybridPetya can compromise the EFI System Partition and deploy a malicious application that encrypts the Master File Table (MFT), the critical metadata structure that keeps track of files on NTFS partitions.
“Due to the shared characteristics of the newly discovered samples with both Petya and NotPetya, we named this new malware HybridPetya.”
— Martin Smolár, Researcher, ESET
“Late in July 2025, we encountered suspicious ransomware samples … suggesting a connection with the infamously destructive malware that struck Ukraine and many other countries back in 2017,” said Martin Smolár, ESET researcher, who made the discovery. “Due to the shared characteristics of the newly discovered samples with both Petya and NotPetya, we named this new malware HybridPetya.”
One analyzed variant was found exploiting CVE-2024-7344, a UEFI Secure Boot bypass vulnerability disclosed by ESET earlier in 2025. The malware uses a specially crafted cloak.dat file to disable Secure Boot on outdated systems, enabling its EFI payload to execute. ESET noted that while its January 2025 publications avoided disclosing exploit details, the malware author likely reverse-engineered the vulnerable component to reconstruct the attack.
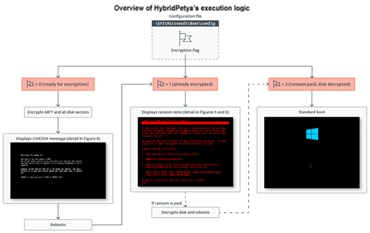
HybridPetya differs from NotPetya in one crucial way: its key-generation algorithm allows attackers to actually provide victims with a decryption key, making it a viable ransomware threat rather than purely destructive malware. At the same time, it lacks the aggressive worm-like propagation that made NotPetya so globally destructive.
ESET’s telemetry shows no signs of HybridPetya being deployed in active campaigns. Researchers caution, however, that whether developed as a proof-of-concept or by a threat actor preparing for future use, the malware demonstrates the ongoing evolution of ransomware toward firmware-level attacks.
For a deeper technical analysis, ESET has published its findings on WeLiveSecurity.com, urging organizations to strengthen their Secure Boot configurations and patch vulnerable systems.


