Ransom payments hit record highs as attackers shift focus from encryption to exfiltration, targeting mid-sized firms and critical sectors
Coveware by Veeam, a global leader in ransomware response and cyber extortion intelligence, has released its Q2 2025 ransomware report, revealing a sharp rise in targeted attacks driven by social engineering and data exfiltration. The findings underscore the urgent need for organizations to bolster data resilience and employee awareness amid evolving threat tactics.
The report highlights a strategic shift among ransomware groups, with attackers increasingly bypassing traditional encryption in favor of stealing sensitive data. Groups like Scattered Spider, Silent Ransom, and Shiny Hunters led the charge, using impersonation and phishing to infiltrate help desks, employees, and third-party vendors.
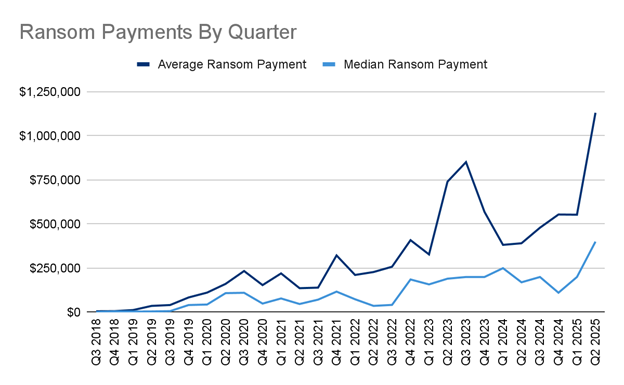
Ransom payments surged dramatically, with the average payout reaching $1.13 million, a 104% increase from Q1, and the median payment doubling to $400,000. Despite the steady rate of organizations paying ransoms (26%), the financial impact has intensified due to exfiltration-only incidents targeting larger firms.
“Attackers aren’t just after your backups – they’re after your people, your processes, and your data’s reputation.”
— Bill Siegel, CEO, Coveware by Veeam
“Data theft is now the primary weapon,” said Bill Siegel, CEO of Coveware by Veeam. “Organizations must treat exfiltration as a frontline risk and not a secondary concern. The human factor remains the weakest link.”
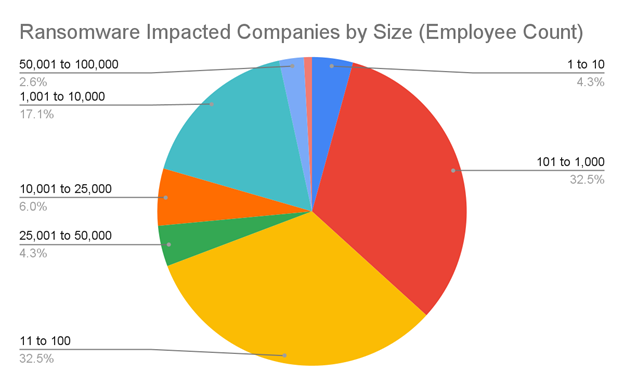
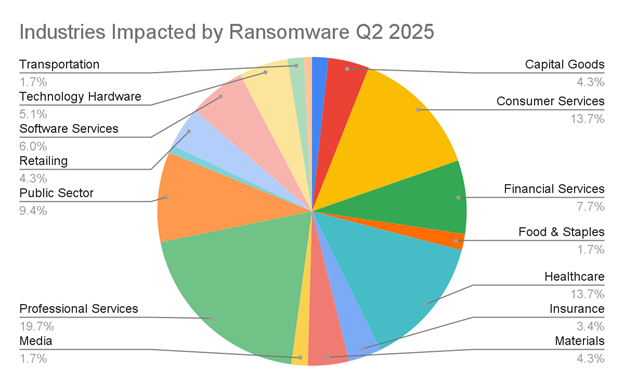
Exfiltration was present in 74% of cases, often accompanied by multi-extortion tactics and delayed threats that prolong the impact of breaches. The most affected sectors were professional services (19.7%), healthcare (13.7%), and consumer services (13.7%), with mid-sized companies (11–1,000 employees) making up 64% of victims.
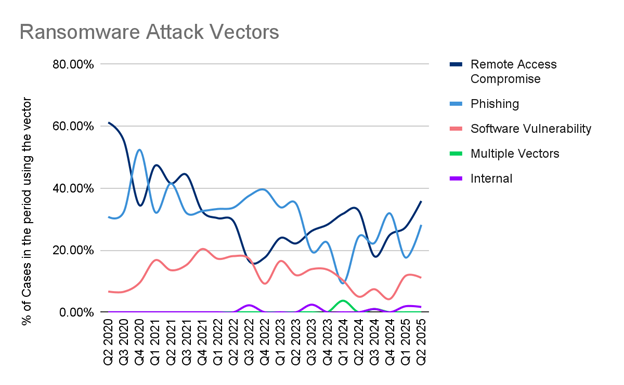
Credential compromise, phishing, and remote service exploitation remain dominant entry points. Attackers continue to exploit vulnerabilities in platforms like Ivanti, Fortinet, and VMware, while “lone wolf” extortionists using generic toolkits are reshaping the threat landscape.
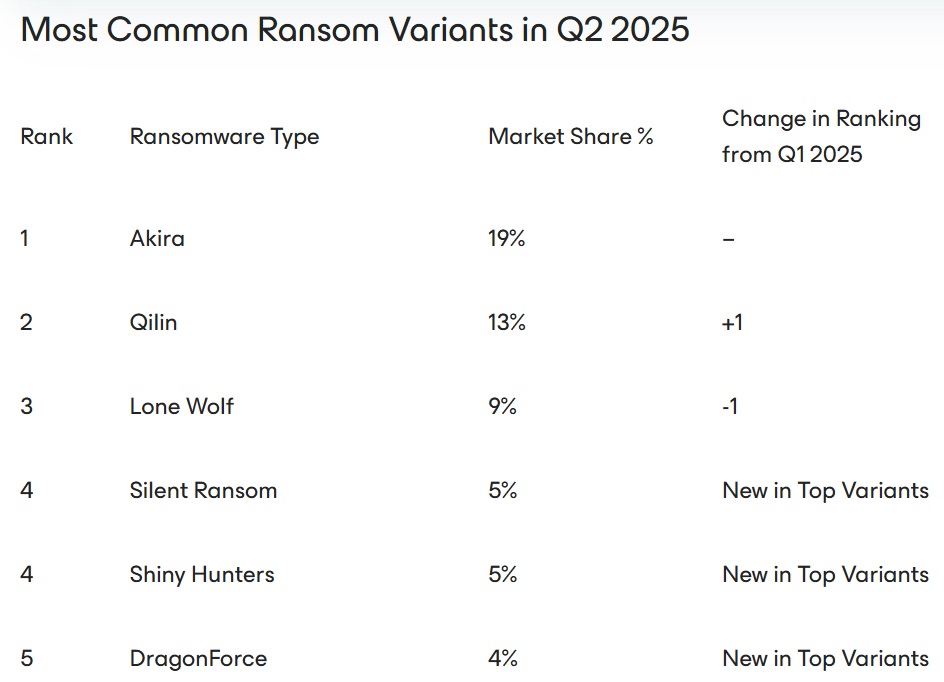
Top ransomware variants for Q2 included Akira (19%), Qilin (13%), and Lone Wolf (9%), with Silent Ransom and Shiny Hunters entering the rankings for the first time.
Coveware by Veeam’s insights are based on real-time incident response and proprietary forensic tools, offering unmatched visibility into ransomware trends. These findings are integrated into Veeam’s broader data resilience offerings, helping customers recover faster and smarter.


